|
Schedule at a Glance (see archives for older entries)
Written assignments should follow the HW guidelines.
|
|
|
T 9/1/15
X
|
First day of class.
|
|
|
W 9/2/15
A
|
HW due: Order a copy of our
primary textbook and our secondary textbook from the list below. Rush
shipping is not required, since there is plenty for us to work on until
everyone has books. You may order the optional books now or, depending on how
far and how fast we proceed, you may postpone those purchases until later.
Primary text (required): Hacking: The
Art of Exploitation, 2nd Edition by Jon Erickson
Note: Be sure to buy the paper
edition of this book, which comes with a CD. Kindle versions are acceptable
for the other books, but not for this one.
ISBN-13: 978-1-59327-144-2
ISBN-10: 1-59327-144-1
Secondary text (required): 24 Deadly
Sins of Software Security: Programming Flaws and How to Fix Them by
Michael Howard, David LeBlanc, and John Viega
ISBN-13: 978-0-07-162675-0
ISBN-10: 0-07-162675-1
Optional book #1 (OK to postpone purchase): The Hacker Playbook 2: Practical Guide to Penetration Testing by Peter
Kim
ISBN-13: 978-1512214567
ISBN-10: 1512214566
Optional book #2 (OK to postpone purchase): Black Hat Python: Python Programming for Hackers and Pentesters, 1st Edition by Justin Seitz
ISBN-13: 978-1593275907
ISBN-10: 1593275900
|
|
|
Th
9/3/15
B
|
No class.
|
|
|
F 9/4/15
C
|
HW due: Order the first two
course textbooks if you have not already done so. The remaining ones are
optional.
In class: Review of unsigned and signed (2’s complement) representations, endianness,
basic hex arithmetic. New material to be discussed: strings, null
termination, floating point, boolean logic, more
advanced hex arithmetic, and 1GL/2GL/3GL.
|
|
|
M 9/7/15
|
No school (Labor Day).
|
|
|
T 9/8/15
D
|
HW due:
Perform each of the following operations in hex (using 2’s complement
arithmetic) as well as decimal. Try to do everything without using the
programmer’s calculator, but you may use the programmer’s calculator at the
end to check your work. Show all work, especially the way in which you are
rewriting the addends and deciphering the final answers. Note: The programmer’s calculator is available in Windows by
running Calc.exe with the ALT+3 view.
The first one is done for you as an example below. Note that we do not use any borrowing in 2’s
complement arithmetic. We simply perform the complementing operation (bit
flip and add 1) whenever we need to change sign. Carries beyond the implied
capacity (i.e., 1, 2, or 4 bytes, depending on the problem) are discarded. If
your final answer has a leading bit of 1 (i.e., a leading nybble
of 8 or more), then you must complement the final answer in order to
determine what negative integer is meant. For example, if your final answer
is 0xF2, that is clearly negative since the lead nybble
is F, and F > 7. Take the complement to get 0x0D + 1 = 0x0E = 14d. Answer:
–14.
1.
0x31
−0x1A
Decimal: 3(16) + 1 – (1(16) + 10) = 49 – 26 = 23
Hex:
Complement of 0x1A is 0xE5 + 1, or 0xE6.
0x31
+0xE6
0x117; discard carry to get 0x17
Check: 0x17 = 1(16) + 7 = 23
2.
0x51
−0x7E
3.
0x310C
−0x18B4
4.
0x310C
−0x68B4
5.
0x78
+0x3F
6.
0x51DB
−0x6C39
7.
0x52AC108E
−0x64B04AF2
|
|
|
W 9/9/15
E
|
No class.
|
|
|
Th 9/10/15
F
|
HW due:
1. Reconfigure your BIOS settings (note:
Intel x86-based architecture is required) in order to get your computer
to boot from a CD. If you use one of the lab PCs, simply press ENTER after
the first splash screen appears, then F12 to display a menu that lets you
choose the CD drive as the boot device.
2. Start tinkering with the default Linux environment (the first choice on
the menu). Try to execute a few of the early exercises. If you have some
prior experience with Unix, execute a few shell commands (such as ls, cd, cat, man, and grep). When you have
had enough, issue the command
sudo shutdown now
and wait for all processes to terminate. When you get a # prompt, it is OK to
remove your CD-ROM and power off.
|
|
|
F 9/11/15
G
|
In class: More on Unix (see
handout),
hash functions, salt, birthday paradox, difference between programming and
shell scripting, and how HBGary got pwned by Anonymous.
|
|
|
M 9/14/15
A
|
HW due:
1. Read the preface and pp. 1-7 in the Erickson text if you have not already
done so.
2. Skim pp. 8-17, all of which should be quite familiar to you already.
3. Read in extreme detail from the middle of p. 17 (beginning with “Also in
C, the compiler must . . .”) through the end of the first paragraph on p. 30.
Use the standard HW formatting
guidelines to write some useful reading notes for yourself. Take your
time.
4. Perform all the exercises in the textbook as they occur, and use the standard HW formatting guidelines
to note any anomalous behavior you see or questions you may have. For
example, at the top of p. 30, Erickson states (in passing) that the “horribly
incorrect value of 3343252480 is the result” when using the wrong endian
order. At that point, as at all other similar points in the text, you should
actually perform the bc -ql
command as shown in the book, so that you can verify that the author was
correct. You should also understand why the inputs shown in the bc -ql command are valid. Why
are certain values being multiplied by 2563 while others are
multiplied by 2562? Where are all those values coming from? You
need to know.
5. As you go through #4, make a “cheat sheet” for yourself so that you will
have something to refer to in the future. This cheat sheet may be included in
your HW paper for #4, or if you prefer, it can be on a separate sheet of
paper. For example, one entry on your cheat sheet might be this:
GDB
command: info register ____
Shortcut:
i r ____
Purpose:
Displays contents of a register.
Any format that you find useful is permitted. You do not need to feel bound
by the verbose 3-line format illustrated in the example above.
Note: Parts 3 and 4 will take a
long time if you do them correctly, and you may not be quite able to finish
them over the weekend (unless you are seized with the “zeal” of tinkering and
hacking, of course). These are the sorts of details that we would skip over
in any other class, because they are nitty-gritty and at times slightly on
the tedious side. However, the discipline of CFCS is that we must sweat the
tiny details that everyone else skips. There is no shortcut to becoming
knowledgeable at a deep level. However, once you catch the “zeal,” it can be
a lot of fun. You’re exploring knowledge that is highly specialized and
rarefied. If, say, 5% of the people in the American workforce are able to
program competently in a language such as C or Java, remember that only a
tiny fraction of those people will
ever understand the kind of material that you’re learning here.
|
|
|
T 9/15/15
B
|
No class.
|
|
|
W 9/16/15
C
|
HW due:
1. If you have not already done so, finish the assignment that was due on
Monday.
2. Read this
Wikipedia article about IEEE floating-point representations, and answer
questions (a) and (b) below. Note:
You will probably need to follow some of the hyperlinks embedded within the
article in order to make sense of the terminology being used.
(a) Explain the first 5 examples in section 1.3 of the article (i.e., the
section entitled “Double-precision examples”). In order to do this, you will
have to understand how the sign bit, 11 exponent bits, and 52 significand
bits (representing a 53-bit significand, since a leading “1” bit is implied
but not stored) are encoded. All of that information can be extracted from
the article. This is great practice for reading technical documentation. If
you get stuck, please come in during Tuesday’s office hours, but it is more
educational if you can puzzle it out on your own. Note: The word “mantissa” is commonly used as a synonym for
“significand,” but as described in the article, this usage of “mantissa” is
deprecated. We will stick to the word “significand” used in the IEEE
floating-point standard.
(b) Encode the floating-point values 1, –3.125, and 2049.75 using the
binary64 standard, which is the same as what we called double in Java. Remember to give all final answers in
little-endian byte order. Include some explanations to demonstrate how you
performed your conversions. Note:
The first one is easy, since the article already gives you the starting
point. The others are somewhat more challenging.
|
|
|
Th
9/17/15
D
|
HW due: Work through pp.
30-43 (through §0x262), using the same ground rules as in the 9/14 calendar
entry.
|
|
|
F 9/18/15
E
|
No class.
|
|
|
M 9/21/15
F
|
HW due: Work through pp.
43-58 (§0x263 through §0x265), using the same ground rules as in the 9/14
calendar entry.
An open-notes quiz is possible today. Topics may potentially include IEEE
floating-point format (binary64, i.e., double in Java), hex, 2’s complement arithmetic, and the
Erickson book through p. 30.
|
|
|
T 9/22/15
G
|
HW due: Finish working with
yesterday’s 222-byte monochrome bitmap, or create a new 40 x 30 bitmap if you
prefer (30 pixels wide, 40 pixels tall). Answer the following questions on
your HW paper:
1. Exactly what is it that fills the 24 bytes from offset 0x26 through 0x3D,
i.e., immediately before the bitmap array begins at 0x3E? Be specific.
2. What is the “alpha channel” (A value) in the color table used for? Be
brief (1 or 2 words preferred).
3. Why are color values stored in the order BGRA instead of the more logical
ARGB (alpha, red, green, blue)?
4. The byte at offset 0x22 tells us that the bitmap array occupies 160 bytes.
However, a 40 x 30 bitmap is 1200 pixels, and a bit depth of 1 bpp (monochrome) should require 1 byte for each 8 pixels,
or 150 bytes total. What explains the 10-byte discrepancy?
5. Use graph paper or a hand-drawn 40 x 30 grid to recreate your bitmap file
manually.
6. Can you recognize your sketch in #5 as being equivalent to the bitmap you
started with? Why or why not? Be specific. (The answer can be found in the
Wikipedia readings.)
7. BONUS (optional): Write a
program in Java, C, Visual Basic, Python, or any other 3GL you wish that will
generate the file for a new, larger bitmap. Monochrome is perfectly
acceptable, but you can get snazzy and try more colors if you wish. (A red,
white, and blue flag, maybe?) Then, use Pbrush.exe to open the file to verify
that your program produced it correctly. Warning:
Save your work frequently, since a malformed .BMP file can hang your computer.
|
|
|
W 9/23/15
A
|
HW due (work on all of
these at home, and be prepared to show some progress on Wednesday, but they
will not be collected until Friday):
1. Do #7 from yesterday’s assignment. Monochrome is acceptable, but you can snazz things up by using one of the color formats.
2. Write a program that accepts a 9-character string input (preferably as a
command-line argument) and creates a data file that represents the saved
state of a tic-tac-toe game in progress. For example, OXOOXX_OX would denote
this nearly completed cat’s game:
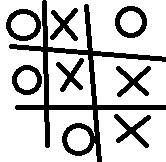
The underscore character denotes an empty cell. We will adopt the convention
that player X always goes first, which means that the next player to play
will be X if the count of X’s and O’s is even, O if odd. The data file that
you create should have a “proprietary” format that only you understand fully.
If you wish, you may include extra features in your file format—for example,
a way of explicitly storing the next player whose turn it will be when play
resumes.
3. Share your executable code only (not
source code) from #2 with your partner, and let him throw as much data at it
as he wishes in an attempt to hack your file format. The ideal format would
be tricky enough to be moderately challenging, but not excessively
convoluted. Try to keep your partner challenged for about half an hour.
Encryption is not permitted.
4. At the same time, attempt to hack your partner’s file format. Your goal is
to learn as much about it as possible. Write a report in which you describe
absolutely everything you think you know about your partner’s file format.
For example, these are just a few of the many questions you should be curious
about:
What length of input string will cause the
program to report an error message (or abend)?
Are any characters other than X, O, and _
accepted in some fashion into the data file?
What numbers, characters, or other bit patterns
(if any) are used to represent X, O and _ ?
At what byte offset are data for each cell
stored, or is some altogether different technique being used?
Is the
“next player to move” stored in the data file? If so, how?
Are there other features that your partner
seems to have incorporated into his format? Can you deduce what they are?
Are there “magic numbers” or seemingly
arbitrary features of the file format? If so, are they always the same? If
they are not always the same, can you figure out why not?
Note: You may make some incorrect
conjectures about your partner’s format. That is certainly OK. However,
remember that once you have formed a conjecture, you learn much more by
throwing potentially disconfirming
test cases at the code than by feeding it test cases that would seek to
confirm or corroborate your conjecture.
Also note: The use of automated fuzzer software to exercise your partner’s code is
permitted but not expected.
|
|
|
Th
9/24/15
B
|
No class.
|
|
|
F 9/25/15
X
|
HW due: See the 9/23
calendar entry. Seniors, please meet with me sometime on Thursday (or first
thing Friday morning, between 7 and 8 a.m.) to show me your work.
|
|
|
M 9/28/15
C
|
No additional written HW is
due. You should finish up your report that was due last Friday, however.
|
|
|
T 9/29/15
D
|
HW due:
1. Modify #7 from your programming assignment in the 9/22 calendar entry
(original due date: 9/23) so that your bitmap is interpreted from upper left
to lower right instead of from lower left to upper right. This should take
only a few minutes. What does the revised output look like now? On your HW
paper, write a brief answer with explanation.
2. Use a programmable calculator, a spreadsheet, or a computer program to
answer probability questions (a) and (b) posed below. You may find the
Wikipedia article on “Birthday attack” to be useful in estimating the answer
for the second question. For the parameters A and B, use the
following values:
Chris: A = 10–4, B = 50
Daniel A = 10–7, B = 50
Edward A = 10–10, B = 50
Ryan A = 10–4, B = 100
Tomasz A = 10–7, B = 100
Zack A = 10–10, B = 100
(a) If a specific hash value of B bits is declared in advance, how
many other hashes are needed before the probability of at least one collision
with that declared value exceeds A?
(Use either a simulation or the formula approach given in class on 9/28.)
(b) If a vast number of B-bit
hashes are computed, how many hashes can there be before the probability that
some pair of hashes will have a
collision exceeds A? (Use the
approximation formula found in the Wikipedia article.)
Note: For parts (a) and (b), assume
that all hash function executions are independent and that the hash function
being used has an essentially uniform distribution over the entire set of
possible hash values.
|
|
|
W 9/30/15
E
|
No class.
|
|
|
Th
10/1/15
F
|
Field Trip to 1150 15th St. NW for the Washington
Post Cybersecurity Summit. Meet at
the service road on Garfield St. (near Grant Meadow) at 7:45 a.m., and we
will travel downtown together. We will be back shortly after 12:00 noon.
Important: Those who are not going
on the field trip (Ryan, Edward, and possibly Zack) are required to view the
livestream video during Block 5 (our normal class period) by clicking here
and looking for the livestream link that is supposed to be posted there
during the event.
|
|
|
F 10/2/15
G
|
HW due: Final version
(typed) of your reverse-engineered tic-tac-toe protocol. Score will be based
on quality of presentation.
|
|
|
M 10/5/15
A
|
HW due:
1. Write approximately 1 to 2 pages of notes summarizing what you saw as the
key points of last Thursday’s cybersecurity summit. If your handwriting is
really small, you may not need to go beyond one page. You are allowed to
refer to the event’s Twitter feed if you need to boost your memory. Use
standard HW format.
2. Read. pp. 89-107 in the Howard/LeBlanc/Viega
textbook (on buffer overflows). Reading notes are required, as always.
In class: Pop quiz (open notes) on buffer overflows.
|
|
|
T 10/6/15
B
|
No class.
|
|
|
W 10/7/15
C
|
HW due: Read Sin 10
(command injection) on pp. 172-182 in the Howard/LeBlanc/Viega
textbook. Reading notes are required, as always. The chapter references the
more detailed information on pp. 4-28, which we will cover later in the
course.
|
|
|
Th
10/8/15
D
|
HW due: Read Sins 11 and 12
(error-handling failures and information leakage) on pp. 184-204 in the
Howard/LeBlanc/Viega textbook.
|
|
|
F 10/9/15
|
No school (faculty
professional day).
|
|
|
M 10/12/15
|
No school (Columbus Day).
|
|
|
T 10/13/15
E
|
No class.
|
|
|
W 10/14/15
F
|
HW due (optional): Read
Sins 13 and 14 (race conditions and poor usability). Mainly, though, enjoy
the beautiful weather and recharge your sleep bank.
|
|
|
Th
10/15/15
G
|
HW due: Read Sins 13 and 14
(race conditions and poor usability) on pp. 206-229 of the Howard/LeBlanc/Viega book.
|
|
|
F 10/16/15
A
|
No additional HW due.
Another open-notes quiz is likely.
|
|
|
M 10/19/15
B
|
No class.
|
|
|
T 10/20/15
C
|
Review day.
|
|
|
W 10/21/15
D
|
Test (100 points) on all material covered this year.
This will be an open-notes, open-book test. Although you are required to know
all the important terminology and notation, there will be no regurgitation of
definitions. (That is a pointless waste of time during an open-notes test.)
Instead, you will be required to make judgments that require knowledge of the
definitions in context. There will also be a section on 2’s-complement
arithmetic (in hex) and endianness, as well as a longer section
(approximately 50% of the test) covering code review with recommendations
that you will have to write.
All 3GL code examples will be in Java. You are not expected to write code,
except that you may need to state code revisions in your recommendations for
the final, long section of the test.
|
|
|
Th
10/22/15
E
|
No class.
|
|
|
F 10/23/15
F
|
Guest speaker: Mr. Dan
Schaupner, CTO of Zeichner Risk Analytics
(zra.com).
|
|
|
M 10/26/15
G
|
No additional written HW
due.
In class: dB, dBV, S/N ratio, quantization noise,
Harry Nyquist, Nyquist’s Theorem, Claude Shannon, and information theory.
|
|
|
T 10/27/15
A
|
HW due: Read Sin 19 (weak
passwords), pp. 280-297 of the Howard/LeBlanc/Viega
book.
|
|
|
W 10/28/15
B
|
No class.
|
|
|
Th
10/29/15
C
|
HW due: Read Sin 8 (C++
catastrophes), pp. 144-155 of the Howard/LeBlanc/Viega
book. This material is highly technical and will not make complete sense if
you have not programmed in C++. Nevertheless, the material is quite readable
for anyone with a Java background and some familiarity with object-oriented
programming. Go for the “big ideas” in this section, not the nitty-gritty.
Quizzing on this chapter will focus on the higher-level objectives. For
example, since STL is referred to on many occasions, you should definitely
know what STL means.
|
|
|
F 10/30/15
D
|
HW due: Write a short essay reflecting on what you have learned
so far this semester in CFCS. You may organize it as a bulleted list if you
wish. Note: Don’t list topic areas;
list facts or concepts that you actually learned. Recommended length is half
a page to one page, handwritten.
WRONG:
I learned about buffer overflows, injection attacks, race conditions, poor
usability, weak passwords, C++ catastrophes, 2’s complement arithmetic,
decibels, and some rudiments of using a Unix shell.
(The essay above is no good, since it
is nothing more than a list of topics.)
BETTER:
I learned that a bit is the smallest unit of information, distinguishing
between two states that can be thought of as 0 and 1. With a collection of n bits, I can represent 2n different patterns by
means of binary encoding. I learned that 210 = 1024 or
approximately 103. I learned that hex (hexadecimal) is a shorthand
notation that lets me represent 4 bits (a.k.a. a nybble)
with a single hex symbol. I became fairly skilled at counting, adding, and
subtracting in hex. I learned what ASCII, STL, and information-theoretic
entropy are.
(This is much better, since it lists
actual facts that the student seems to know quite well. However, it is
incomplete, because it omits any awareness of the circumstances under which
an injection attack can occur, the role of the IP, the overarching importance
of code review, TOCTOU, etc. Maybe the student didn’t learn those things as
well as the others, but surely he learned something about them. This student
also forgot to mention anything about our field trip downtown and our guest
speaker.)
|
|
|
M 11/2/15
E
|
No class.
|
|
|
T 11/3/15
F
|
HW due: Generate two (2) or
three (3) possible project concepts. Your project concepts should meet the
following requirements:
1. Interesting—no, scratch that—highly
interesting to you personally.
2. Related to the general theme of coding for cybersecurity. (No policy
studies, please, unless there is a strong technical or coding angle that
applies.)
3. Moderately challenging for you, given your current state of knowledge. Note: That means that some projects
that are suitable for some people would be too easy or too hard for others.
Choose a project concept that is moderately challenging for you personally.
4. Something that can be wrapped up by December 11 despite all the other
things you have going on at that time of year. You should plan on submitting
a draft by December 11. Your draft will be reviewed with suggestions, and
then you will submit a final copy before leaving for Christmas break on
December 18.
Note: You are not committing to a
project concept at this time. Your assignment for Tuesday, 11/3, is simply to
write down some ideas for discussion. We will work together as a class to
flesh out the project concepts and make sure that everyone has something highly interesting and feasible to
work on. If project topics need to be adjusted or changed later, that is
fine, but we need to start thinking about the project now.
Pairs project concept proposals will be considered, but a pairs project
should have synergy. In other words, it should not merely be a way of
dividing the workload. If you write a pairs proposal, you should be prepared
to explain precisely why the pairing arrangement will provide a good
opportunity for both students to learn more than either student would learn
by working alone.
“But what if I can’t think of
anything?” Don’t worry! Here is an alternate assignment for you if you
are stuck.
Write out the answers to these preliminary questions as a way of getting some
thoughts flowing . . .
1. Would you prefer to work
alone or with a partner?
2. Which do you like
better, simulated offense or simulated defense? Why?
3. Would you like to
research a classic attack from the past, or would you rather try to blaze a
new trail?
4. Are you more interested
in the mathematical/abstract side, or the computer/engineering/practical
side?
5. Do you prefer scripting
languages, high-level languages like Java and C++, or assembly-level code
(bits and bytes)?
6. For the moment, imagine
that you could do anything you wanted with a computer. Don’t get bogged down
by whether it is actually feasible with today’s technology or whether you
have the skills to make it happen. Just ask yourself, “If I could do anything
I wanted with a computer, what would
it be?”
If you can’t think of any
actual project concepts, focus on finding a clear answer to each of the 6
questions above—written out on paper—so that the rest of us can brainstorm
some project ideas for you when we meet in class.
|
|
|
W 11/4/15
G
|
HW due:
1. Read Sin 21 (wrong cryptography), pp. 316-333 in the Howard/LeBlanc/Viega book.
2. Generate one (1) additional project concept that might be of interest to
Edward Z.
|
|
|
Th
11/5/15
A
|
HW due:
1. Read Sin 20 (weak random numbers), pp. 300-314, and be prepared for
quizzes on both Sins 20 and 21.
|
|
|
F 11/6/15
|
No school (teacher work
day).
|
|
|
M 11/9/15
B
|
No class.
|
|
|
T 11/10/15
C
|
HW due: Read Sin 22
(failure to protect network traffic), pp. 338-346. This is a shorter reading
assignment than usual. However, you are expected to search for terms that are
used without explanation in the text (such as IPv4 and IPv6) so that you can
have an understanding of what is being discussed.
|
|
|
W 11/11/15
D
|
HW due: None. This is a
rare night off without an additional assignment. If you have extra time, use
this opportunity to consolidate previously studied material.
In class: Hamming 7,4 decoding of the following 14 partially garbled bytes,
which carry an 8-byte ASCII payload: 0xCB393608D9510182375518D73B29
|
|
|
Th
11/12/15
E
|
No class.
|
|
|
F 11/13/15
F
|
HW due: Finish decoding the
14 partially garbled bytes that were given in class on Wednesday.
Simplified procedure:
1. For each block of 7 bits, compute the parity of bits 4, 5, 6, and 7 (numbered
from 1 at left to 7 at right). Call this result K.
2. For each block of 7 bits, compute the parity of bits 2, 3, 6, and 7. Call
this result L.
3. For each block of 7 bits, compute the parity of bits 1, 3, 5, and 7. Call
this result M.
4. The 3-bit sequence KLM, interpreted as a binary number, tells the position
of the bit that was flipped.
Often, the flipped bit turns out to have been a parity bit. However, in
situations where a data bit was flipped, the message can change dramatically.
|
|
|
M 11/16/15
G
|
HW due: Read Sin 7 (integer
overflows), pp. 120-142 in the Howard/LeBlanc/Viega
book.
|
|
|
T 11/17/15
A
|
HW due: Read Sin 4 (magic
URLs, predictable cookies, and hidden form fields), pp. 76-86 in the
Howard/LeBlanc/Viega book. This one’s a lot shorter
and easier to digest.
Note: Today’s quiz may also include
some “leftover” questions from Sin 7, especially on 2’s complement integer
encoding.
|
|
|
W 11/18/15
B
|
No class.
|
|
|
Th
11/19/15
C
|
HW due: Read through the key exchange worksheet so
that you are familiar with the project that you will be working on in class.
In class: Work on the key
exchange worksheet with a partner.
|
|
|
F 11/20/15
D
|
In class: Guest speaker,
Mr. Joe Morris of MITRE Corporation.
|
|
|
M 11/23/15
E
|
No class.
|
|
|
T 11/24/15
F
|
FFun Day (no additional written HW due).
|
|
|
M 11/30/15
G
|
HW due: Begin working on
your project. Target date for overall completion is Friday, Dec. 18. The only
person who has any written work due today is Edward, who should prepare a
written project proposal (approx. 2 paragraphs).
|
|
|
T 12/1/15
A
|
HW due: Work on your
project.
|
|
|
W 12/2/15
B
|
No class.
|
|
|
Th
12/3/15
C
|
HW due: Work on your
project.
|
|
|
F 12/4/15
D
|
HW due:
1. Read and work through all of topic 0x266 (pp. 58-61) in the Erickson text.
2. Continue working on your project.
|
|
|
M 12/7/15
E
|
No class.
|
|
|
T 12/8/15
F
|
HW due:
1. Read and work through all of topics 0x267, 0x270, and 0x271 (pp. 62-77) in
the Erickson text.
2. Continue working on your project.
|
|
|
W 12/9/15
G
|
HW due: Since we did not
have enough class time set aside on Tuesday for you to make much progress,
there is no additional assignment for today other than to work on your
project.
|
|
|
Th
12/10/15
A
|
HW due:
1. Read and work through all of topics 0x272 and 0x273 (pp. 77-81) in the
Erickson text.
2. Continue working on your project.
|
|
|
F 12/11/15
B
|
No class.
|
|
|
M 12/14/15
C
|
HW due:
1. Read and work through all of topics 0x280 through 0x282 (pp. 81-88) in the
Erickson text.
2. Continue working on your project. Target completion date is Friday, Dec.
18.
|
|
|
T 12/15/15
D
|
HW due: Continue working on
your project.
In class: Review for Quiz Event.
|
|
|
W 12/16/15
E
|
No class.
|
|
|
Th
12/17/15
F
|
Quiz Event.
This will be more painful than a typical daily quiz, but less painful than a
full-blown test.
|
|
|
F 12/18/15
G
|
HW due today:
1. Question 4 from yesterday’s Quiz Event. Allow approximately 20-25 minutes
for this. (You didn’t have time during class, because the Quiz Event started
late, and that was my fault.)
2. Submit a written project report (target length: 2-4 pages). Your report
should describe what you did, what
resources you consulted, and what you learned in the process. The tone
can be informal, since this is not a report intended for a larger audience.
However, your grammar and spelling should be correct. A PowerPoint slide
presentation to supplement your written report is optional.
If you need more time for your project, that is acceptable. In that case, simply
give an oral report of what you have accomplished so far. Extensions, if
required, will be considered on a case-by-case basis. Completing your project
by this day will allow you to have a pleasant and restful Christmas break.
|
|
|
M 1/4/16
A
|
HW due: Please read and be
prepared to discuss both of these recent articles:
https://www.propublica.org/article/fact-checking-the-debate-on-encryption
https://www.washingtonpost.com/news/in-theory/wp/2015/12/15/how-the-nsa-tried-to-build-safe-encryption-but-failed/
Optional HW: Take a look at this video of a tiny
portion of the Mandelbrot set.
|
|
|
T 1/5/16
B
|
No class.
|
|
|
W 1/6/16
C
|
Be prepared for a graded
discussion or closed-notes quiz on the two articles whose links were posted
in Monday’s calendar entry.
In class: Review for midterm exam.
|
|
|
Th
1/7/16
D
|
HW due: Start working on
your midterm exam cheat sheet. Bring it to class; as long as you have made a
start on the process, you will get credit for this HW assignment. Space
limitation is one standard sheet of paper (8.5 by 11 inches), lined or
unlined. You may use both sides if you wish.
|
|
|
F 1/8/16
E
|
No class.
|
|
|
M 1/11/16
|
Midterm Exam (20% of your semester grade), MH-108,
11:00 a.m. to 1:00 p.m.
|
|
